As digital threats grow and evolve, cybersecurity is becoming more vital for businesses of all sizes. Cybercrime trends are shifting, with hackers now targeting not just large corporations but also small and medium-sized businesses and even individual employees.
Our article focuses on the latest cybersecurity trends, providing strategies for companies to safeguard their data and infrastructure. We emphasise the importance of employee cybersecurity training and partnering with trusted cybersecurity providers.
Global Cybersecurity Issues
As businesses accept digital transformation, the importance of cybersecurity has reached a maximum level. The increased use of cloud computing, widespread adoption of mobile devices and the integration of AI technologies have collectively created more opportunities for cybercriminals.
Based on projections outlined in Statista’s Cybersecurity Outlook, the anticipated global cost of cybercrime is going to increase over the next five years. It’s expected to climb from US$11.50 trillion in 2023 to US$23.84 trillion by 2027.
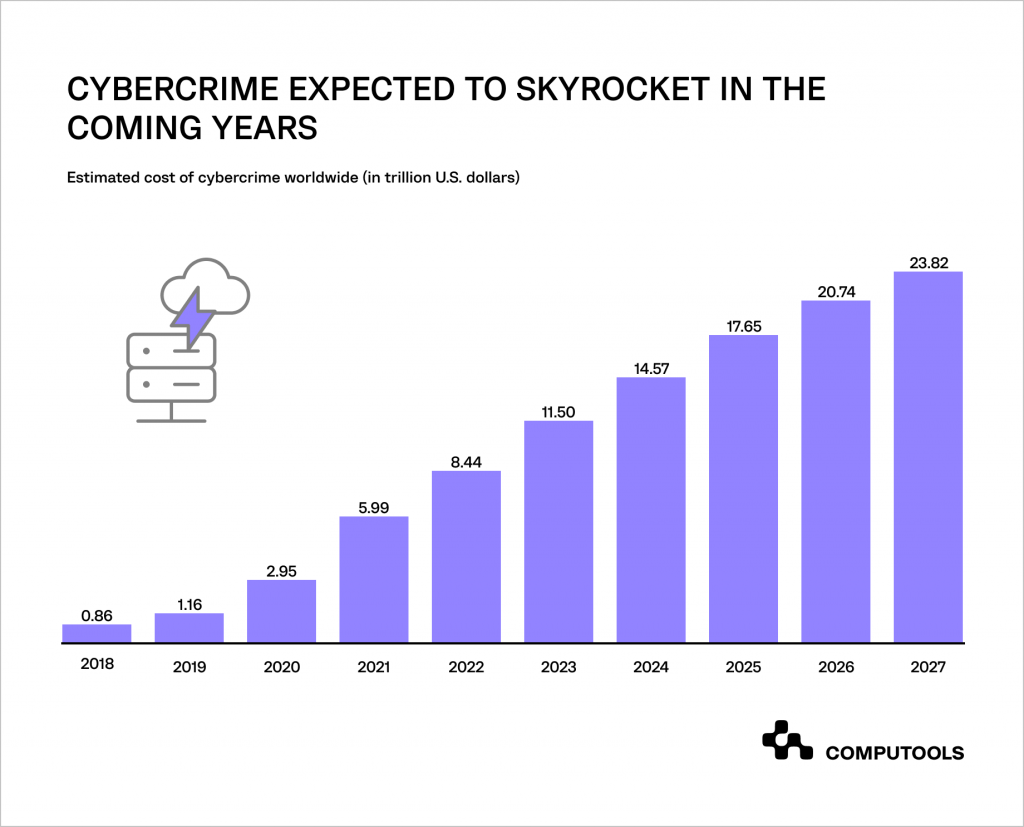
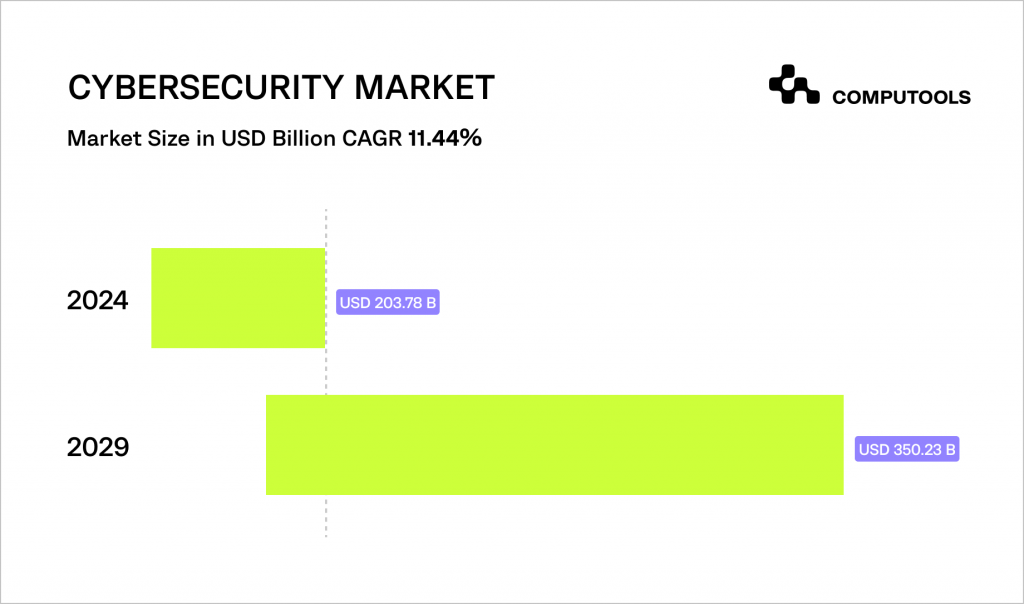
As a response to this, the market for cybersecurity technologies is also anticipated to experience substantial growth, projecting an increase to US$350.23 billion by 2029.
This highlights the growing significance of cybersecurity in safeguarding networks, information and personal data from the ever-increasing threat of cyberattacks.
One of the main reasons behind the increase in cyberattacks is the scarcity of well-trained professionals across different industries. Particularly in Europe, Asia, Latin America and the Middle East, there is a notable shortage of talent.
This creates a challenge for banking institutions, government organisations and industrial businesses in effectively countering cybersecurity threats.
The escalating rate of cybercrime is also partly fuelled by the rapid development of generative artificial intelligence. While platforms like ChatGPT drive digital innovation, they also equip cybercriminals with sophisticated tools.
Generative AI’s ability to quickly recognise, summarise and generate realistic content, including convincing ‘deepfakes’, enhances the scale of cyber campaigns like phishing, business email compromise and disinformation.
The impact of a single cyberattack on a business can be devastating, leading to data and intellectual property loss, legal liability and significant financial losses. According to Statista’s research, manufacturing is the most targeted industry worldwide, accounting for nearly 25% of cyberattacks, followed by finance, insurance and professional, business and consumer services.
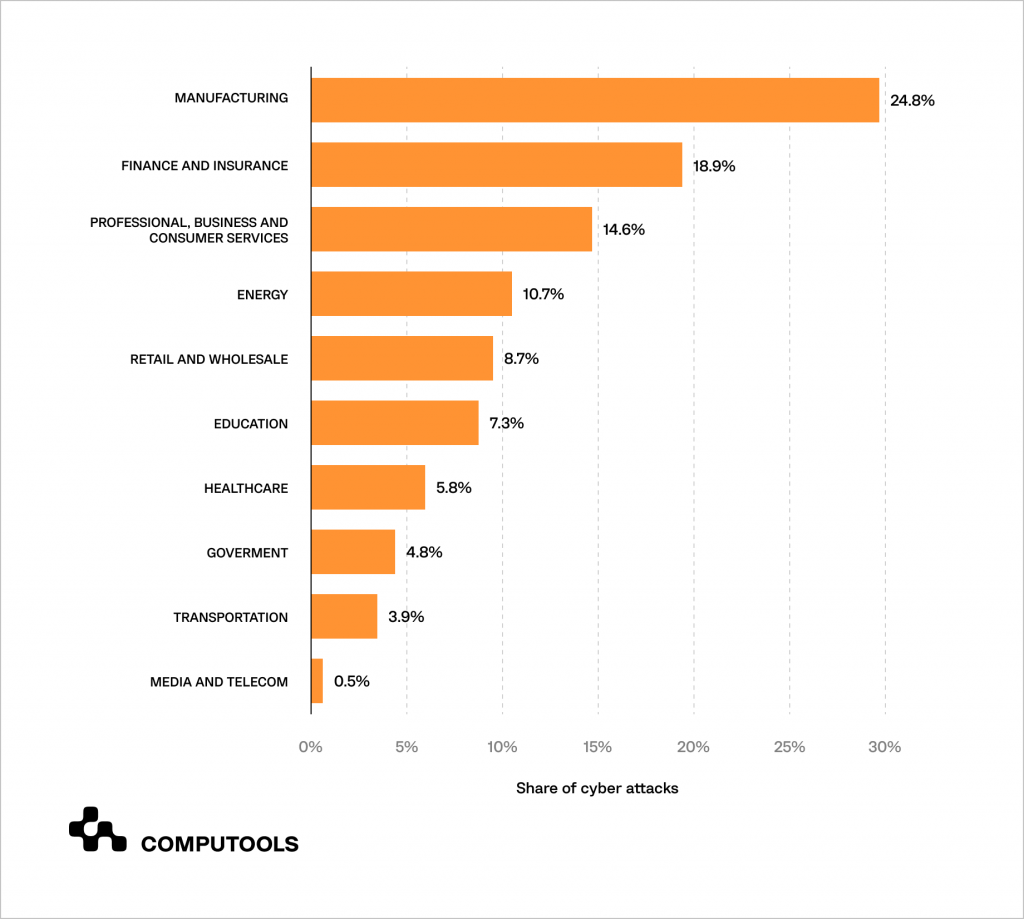
The aftermath of a cyberattack can disrupt a business for weeks or months, with reduced productivity and reputational damage. However, businesses can turn this challenge into an opportunity.
Leaders can see significant improvements by making simple process changes, properly educating employees and staying informed about data security trends. In the following sections, we’ll outline essential trends your team should know about to improve your cybersecurity defence.
Cybersecurity Trends in 2024
With the advancement of technology, cybercriminals are also evolving their tactics. In this exploration, we examine key cybersecurity trends shaping the landscape in 2024 and beyond.
Small Business Cybersecurity Challenges and Solutions
1. Limited resources and budget
As per a Vade survey, 63% of IT decision-makers recognise a lack of resources when aiming to enhance cybersecurity for small businesses. For rapidly growing companies, where teams are often stretched thin, optimising time, resources and budget becomes the main task.
Unfortunately, this shortage typically limits businesses’ ability to ensure the necessary level of protection and implement changes or recommendations.
Solution: Artificial intelligence and machine learning
Small businesses can explore cost-effective AI-driven tools for threat detection and response. A notable trend in the industry is AI-driven threat hunting, where machine learning actively seeks potential breaches by analysing patterns in extensive datasets
AI-powered security and automation platforms are also simplifying incident response, minimising human intervention and reducing response times.
Moreover, AI-based user behaviour analytics enhance identity and access management, ensuring that only authorised personnel can access sensitive information.
2. Lack of employee training
The human factor often emerges as the vulnerability in cybersecurity, with employees serving as potential weak links. For small businesses, the challenge lies in the limited expertise to consistently offer training on optimal cybersecurity practices.
Solution: E-learning platforms
Learning platforms provide engaging and current cybersecurity training, using interactive scenarios that are relevant to the specific needs of a business. Plus, their content can be regularly updated to keep pace with the latest cybersecurity innovations, ensuring that the business’s defences remain strong.
These platforms are also cost-effective and scalable, eliminating the need for costly in-person training sessions. The primary investment in cybersecurity of 46% of companies involves enhancing the skills and knowledge of their cybersecurity and IT personnel.
3. Remote work vulnerabilities
With the increase in remote work, small businesses face new challenges. Remote work can expand the attack surface, as employees use personal devices and unsecured networks, making it harder to enforce security policies and protect sensitive data.
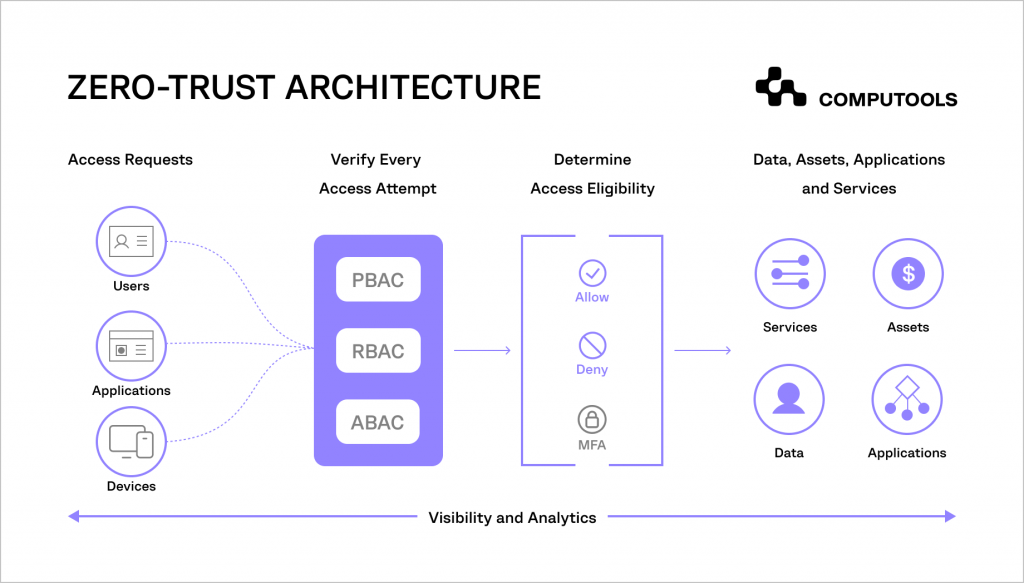
Solution: Zero trust security models
Zero trust frameworks will soon become mandatory in numerous sectors, as traditional defences like VPNs and firewalls prove inadequate against sophisticated attacks.
Zero trust architectures involve rigorous validation of every user and system by using stringent multifactor authentication and least privilege permissions.
It also includes micro-segmentation to limit connectivity and continuous monitoring to spot unusual behaviours.
According to the survey, 41% of business leaders have already reported the implementation of zero trust architecture principles in their organisations.
Early adoption of zero trust principles, guided by frameworks like ISO 27001, helps SMBs strengthen their defences and drive innovation.
Medium Business Cybersecurity Challenges and Solutions
1. Advanced persistent threats (APTs)
Medium-sized enterprises are increasingly targeted by sophisticated APTs, prolonged cyberattacks aimed at stealing data over time.
These businesses often have more valuable data than small businesses but less robust security than large corporations, making them attractive targets.
Solution: Threat detection systems and continuous monitoring
Threat detection software solutions for businesses quickly analyse large volumes of data to detect anomalies and patterns indicative of cyberattacks, such as unusual login attempts or unexpected data transfers.
For instance, an AI-based system can identify ransomware attack signatures, alerting security teams or automatically blocking malicious activities.
Complementing this, continuous monitoring of the network ensures real-time detection of suspicious actions. This involves scrutinising data flows, system logs and user activities to maintain a comprehensive view of the IT environment.
2. Supply chain vulnerabilities
Organisations need to carefully evaluate their third-party vendors and suppliers, ensuring due diligence beyond just trust. Supply chain attacks, both software- and hardware-based, can be catastrophic.
While companies can update their software, ensuring that all suppliers and their networks do the same is critical.
Often, companies are unaware of the components in their software, and a single vulnerability in the supply chain can put everyone at risk.
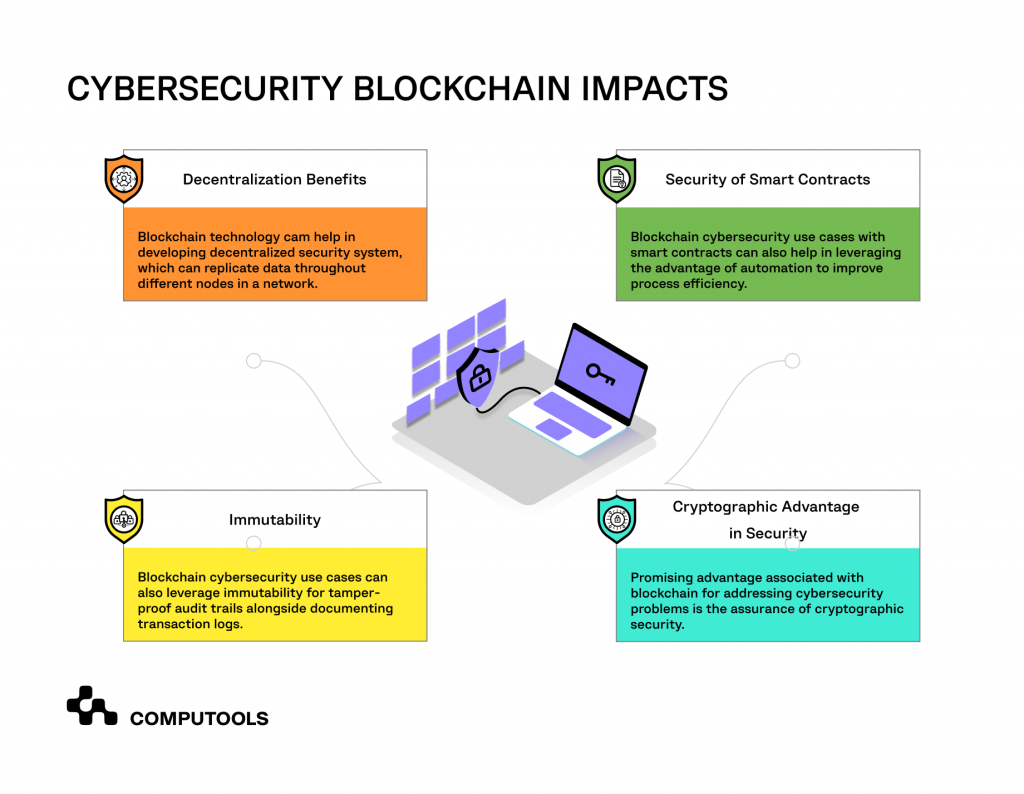
Solution: Blockchain technology
Blockchain improves supply chain security through its transparent, immutable and decentralised ledger system. It securely logs and verifies transactions across a network, making data alteration extremely difficult.
Moreover, the immutability feature of blockchain means that once data is recorded, it cannot be changed retroactively.
In the event of a supply chain disruption or a security breach, blockchain can help quickly identify the source of the problem, as every transaction and transfer is permanently recorded.
3. Insider threats
As the workforce size increases so does the risk of insider threats, either through malicious actions or accidental breaches by employees. Managing these risks while maintaining a positive workplace culture and employee privacy can be challenging.
Solution: User and entity behaviour analytics (UEBA)
UEBA is a cutting-edge data security approach that employs advanced algorithms and machine learning techniques to monitor and analyse the behaviour of users, routers, servers and endpoints.
The primary function of UEBA is to identify unusual or suspicious activities. For instance, if a user who typically downloads small files suddenly starts downloading large volumes of data, UEBA systems flag this as an anomaly.
UEBA can also spot signs of a potential cyberthreat, like a distributed DDoS attack, indicated by a sudden spike in server requests.
Enterprise Cybersecurity Challenges and Solutions
1. Ransomware
Ransomware stands out as a major worry for organisations and the emergence of ransomware-as-a-service further intensifies this global concern.
Today, we’re confronted with ransomware attacks that are notably more advanced than those of a few years ago.
At the same time, malware has become smarter and more challenging to detect, presenting difficulties for standalone automated security tools.
Solution: Advanced endpoint protection
Advanced endpoint protection involves deploying comprehensive cybersecurity technologies at each endpoint – which includes laptops, desktops, mobile devices and other network endpoints.
It uses a combination of traditional security measures, such as antivirus and anti-malware tools, with more sophisticated techniques like behavioural analysis.
Additionally, advanced endpoint protection often includes features like sandboxing, where suspicious files are run in a safe, isolated environment to check their behaviour without risking the main system.
2. Phishing
Phishing remains an ongoing challenge for organisations of all sizes, with no company or employee immune to these attacks.
These attacks, which trick employees into revealing sensitive information, come in various forms, including email phishing, spear phishing, whaling and vishing.
Organisations face a multifaceted challenge in defending against these cybersecurity threats.
Solution: Multifactor authentication (MFA)
MFA continues to be a part of effective cybersecurity strategies, now incorporating biometric technologies such as facial recognition and fingerprint scanning to boost both security and user experience.
Additionally, adaptive authentication, which tailors security measures based on perceived risks, is gaining traction.
Concurrently, there is an increased focus on educating users about the importance of MFA and its role in enhancing security. These developments in MFA are important for organisations looking to ensure the security of their sensitive systems.
3. Data breaches and data privacy compliance
Enterprises hold vast amounts of sensitive data, making them attractive targets for data breaches. Complying with global data privacy laws like GDPR and CCPA adds an extra layer of complexity to their cybersecurity strategies.
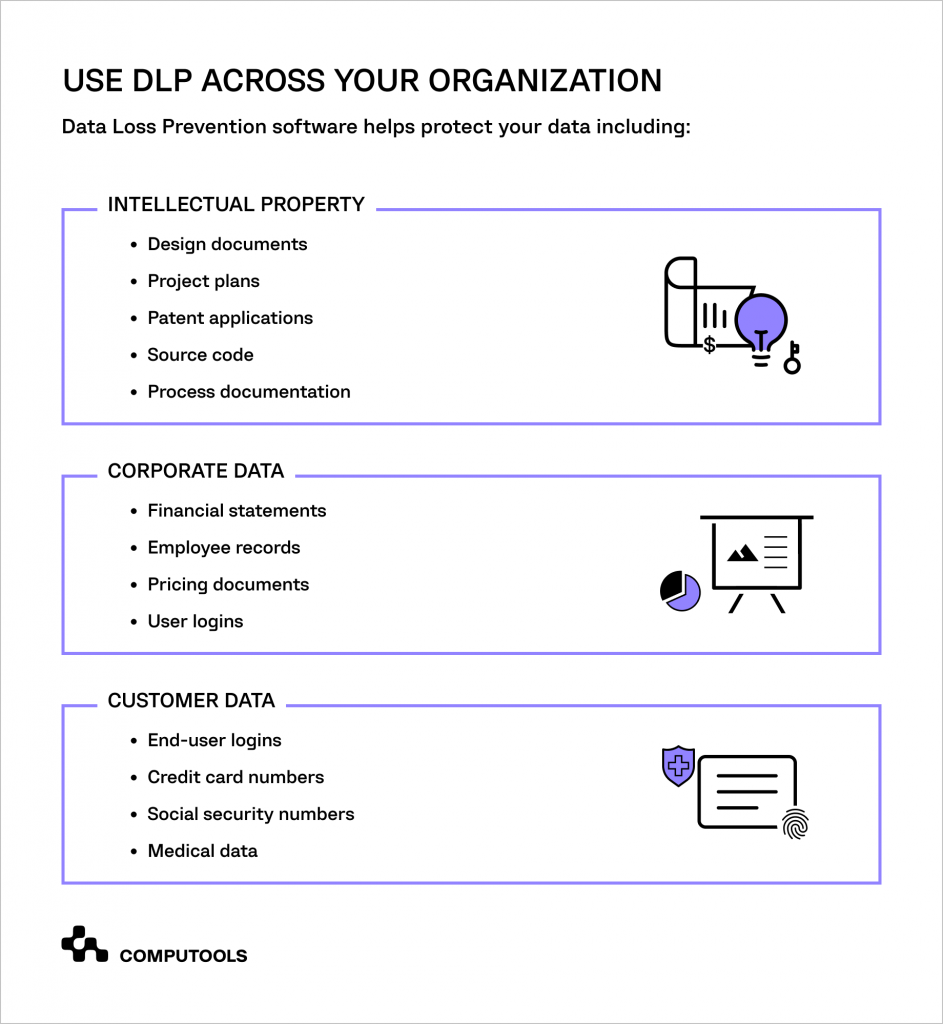
Solution: Data loss prevention (DLP) tools and encryption as a service (EaaS)
DLP tools are designed to detect potential data breaches and prevent them by tracking, identifying and preventing sensitive data leaks while it’s being transmitted, stored and utilised.
They are particularly useful in enforcing compliance with data privacy laws, as they can be configured to identify and protect specific types of sensitive information, such as personal identification information, financial data, or health records.
On the other hand, encryption as a service (EaaS) offers a flexible, cloud-based approach to data security.
EaaS platforms provide encryption of data in transit and at rest, ensuring that sensitive information is unreadable and therefore useless to unauthorised users who might intercept it.
When combined, these technologies form a robust defence against data breaches and a strong foundation for data privacy compliance.
Guidance for Business Leaders to Enhance Cybersecurity
Given the current cybercrime landscape and the increasing demands for strong governance and resilience from regulators, the role of executives in overseeing cyber-risk management has never been more important.
To enhance your organisation’s cyber resilience, consider these actions:
1. Create a thorough cybersecurity strategy
Develop a comprehensive plan to protect against cyberattacks. This plan should include staff training, regular software updates and consistent data back-ups. Having a solid strategy in place enables a quick response to cyber incidents.
2. Partner with a reliable software development services provider
Collaborating with a trusted technology partner can significantly improve your cybersecurity posture. Choose a provider with experience in your industry, as subject matter experts will be invaluable in developing a customised security plan, deploying advanced security solutions and providing prompt responses to cyber incidents.
This partnership ensures that your business is well protected and your cybersecurity goals are met.
3. Provide staff cybersecurity education
Employees can unintentionally become weak points in your cybersecurity defences. Educational programmes should focus on recognising and responding to threats, such as phishing and social engineering. Well-informed employees can help to reduce the chance of a cyberattack.
Conclusion
Cybersecurity remains a significant concern for businesses of all sizes. With the increasing frequency of cyberattacks and the growing complexity of the digital environment, companies must be vigilant in safeguarding their data and infrastructure by collaborating with reliable software partners for effective outcomes.
Feel free to contact us today at info@computools.com to learn more about how we can enhance the security of your business.

Computools
Software Solutions
Computools is a digital consulting and software development company that delivers innovative solutions to help businesses unlock tomorrow.








“Computools was selected through an RFP process. They were shortlisted and selected from between 5 other suppliers. Computools has worked thoroughly and timely to solve all security issues and launch as agreed. Their expertise is impressive.”